Third Time's the Charm: My Journey to Pass the OSCP

After 260 days, 740 hours of studying, and 3 exam attempts I can proudly say I am OSCP certified! It took longer than anticipated, and the journey was not what I envisioned when I started a little over 8 1/2 months ago. It took pwning 49 PWK Lab Machines, 26.5 Proving Grounds (PG) Practice machines, watching 77 ippsec videos, and 120+ hours of PWK Exercises and Lab Report creation in order to get 80 points to pass the exam.
While I definitely went into the course with the hubris that I would be one of the folks who passed on their first attempt - despite an (unofficial) 20% passing rate - I'm appreciative of the journey and everything that occurred to finally receive that glorious confirmation email. Below are my thoughts on my exams, what I learned - other than how to hack, and what's next. I didn't write an AAR after my second exam attempt, but there will be thoughts peppered in throughout that cover what I learned both leading up to and after my second exam.
Try #3 - The 24-hour Exam
Thoughts on my 3rd go, with some ramblings from attempt #2
I was actually extremely calm - some might even say... ZEN... going into the third exam attempt.

I had learned from my first attempt that it was better for me to start the exam in the late morning. During my second attempt - it helped to be able to sleep in a bit, wake up and have a normal-ish morning routine before the exam, and about ~10-12 hours of hacking before I would naturally start to get tired. I also had the benefit/curse of scheduling my 3rd attempt 2 months in advance, so I had a wide range of dates and start times to choose.
Upon receiving the e-mail with the exam information, I was off to the races. This was my second attempt at the new exam format. I was fortunate enough to receive an extra 7th machine- which is indicative of a debugging machine provided for a buffer overflow, much to my delight. Yes - I never would've thought before taking the PWK that I would actually understand a buffer overflow - let alone actively hope I was provided a buffer overflow attack vector for my exam. On my first attempt (old format), the buffer overflow machine was actually the only machine I had successfully pwned, and I didn't have a buffer overflow attack vector on my second attempt.
While I had autorecon running on all of the machines I focused on the buffer overflow. I meticulously documented each step, as I wanted to ensure I had the necessary screenshots for my Exam Report necessary to meet their "copy/paste" exploit replication requirement. I wound up finishing the exploit and getting an initial foothold on the vulnerable machine in ~2.5 hours. I ran into a slight snag when I was validating bad characters which required me to backtrack. This caused me to take a bit more time than anticipated. Regardless, I had my first 10 points of the exam (20 points total when factoring in the lab report).
After some poking around on the machine, and some initial priv esc enumeration I moved onto the Active Directory set. Going into the exam, I had prepped in the PWK lab and completed both the SV and the XOR Domains 3x each. Once, during my initial 90-days access to the labs, and then two more times between my first and second exam attempts. The second time pwning the domain, I tried to repeat the steps without referencing any old notes. On the third attempt, I tried to approach it from an alternative perspective and see if there were ways to obtain Domain Admin access other than my initial attack vector/priv esc paths. On my second exam attempt - and first attempt with the new AD format - I made the mistake of ignoring the KISS principle, and left 40 points on the table because I totally overthought the simplest path towards pivoting.
The AD chain I received this go around was much more straight forward. After some initial enumeration I was able to identify the most likely attack vector. After some initial prodding at the application, thinking I was unsuccessful - I was able to do a bit more research, and find what I thought was the source code from the application. I was able to review the source code to better understand the error messages from the exam machine. Fortunately, despite the errors, my exploit path was successful. Sure enough - I found my web shell right where I was expecting. I used that to establish an interactive shell and obtain my first AD flag.
While the priv esc attack vector seemed straight forward, I was unsuccessful in getting an elevated shell with my first handful of attempts. I decided to take one last crack at it, and let the exploit run while I took a break. Sure enough - when I came back I had a wonderful shell as `NT AUTHORITY\SYSTEM`, and my first `proof.txt` of the AD domain. I celebrated with one of my awkward, uncoordinated shell dances that probably looked something along the lines of:
I pillaged the box a bit using everyone's favorite cat to find some goodies that I used to pivot to the second machine in the domain and my second `proof.txt`. From here it was rather straight forward - using similar tactics to pivot and pillage within the domain until I finally recovered all flags within the domain - including the Domain Controller. All in all, it took about ~ 4.5 hours to pwn the domain. I was in great shape - with 60 total points in the first 7 hours of the exam.
Within the next hour, I was able to get a foothold on my second standalone machine thanks to some enumeration to find an exploit that needed a slight venomous tweak. This too - was another machine that the required the exploit to be run a few times before executing successfully. However, given the service/application - I thankfully tried it a handful of times before giving up, and was successful in getting a foothold. I had the local.txt flag - AND ENOUGH POINTS TO PASS. I couldn't believe it. I had never imagined I would pass so quickly. I went from running out of will on my first attempt, to running out of time on my second, culminating with having enough points the exam with 16 hours to spare on my final attempt.
Even though I had enough points to pass, this included the 10 bonus points from the lab report. I wanted to ensure I had a bit of a buffer, so I continued on. From there, I enumerated a bit more, and tried the most the attack path for priv esc.
Within 9 hours from my exam start time I had all of the eventual flags I wound up submitting for my exam. While I still spent time hacking and trying to priv esc on my buffer overflow foothold, and get access to the third standalone machine I didn't try to overdo it. I did the hacker's equivalent of a running back having a breakaway run with under a minute to play with the lead in hand and sliding down at the one yard line to ensure the win. That is - I triple checked all of my exploit steps, ensured I had the necessary flags both in my notes and the control panel, and actually got some sleep. I had previously only slept 90 minutes on my second attempt, but instead I got what felt like a longggg 4.5 hours of sleep this time. Those hypothetical Fantasy PWK Players might've hated me, but I now had the opportunity for the second phase of the exam - to write the report within 24 hours.
Writing the Report & Elation
This section isn't going to be too long, but I did have a few thoughts I wanted to share. Firstly - it took longer than anticipated to complete the report. While it didn't take the full 24 hours to write the report, I submitted it with less time leftover than I was anticipating. I might've been obsessing over the formatting and the small details. Part of it might've been due to my choice of using Joplin to write the report in lieu of Word/LibreOffice. That being said, the vast majority of my time spent was rereading my report. I probably had written the draft of the report within a few hours. The rest of my time was spent had rereading the report (~6-7 times). However, I wanted to make sure the document was formatted properly, the instructions made sense, and the vulnerability summary and remediation recommendations were professional.
Secondly, be sure to read the exam instructions on how to upload the report. I had done so a few times before. However, it definitely can be a tad bit stressful when you get to this point. It would suck to fail the exam because you didn't format the document name properly, or didn't properly validate the MD5 sum of your file after upload. When I read these sections I thought "ehh this is FUTURE Zentester's problem, he'll just read this in more detail later." While I knew the steps well, I would've benefited from a greater familiarity with the steps.
I submitted the report by ~10 AM local time. After which, all the thoughts rushed through my head about ways that I dorked it up and how I could possibly lose 20+ points. Offensive Security has up to 10 business days to review your report. However, I was both surprised and relieved to check my e-mail the following afternoon to see I had passed the exam and finally accomplished my goal. I can now proudly say I'm OSCP certified.
Lessons Learned
Reflecting on my development from 8.5 months ago until now has been tremendous. The pedagogy of the Pentesting with Kali course and labs is arguably best in industry. The course teaches you not only the foundational skills necessary of a penetration tester, but also refines your ability to research and learn. I felt I had grown each time I failed, and exponentially learned more between each exam attempt, despite less prep time between each exam compared to my initial attempt.
Just do the damn thing
In the words of Arnold Schwarzenegger
If I could do it again, I would've signed up for the OSCP sooner. I've wanted to be a hacker for at least the past 7+ years. I had heard about the OSCP shortly after. I had started to "seriously" prep for the exam starting in 2019 after hearing a presentation at BSidesDC. However, that "serious" prep was honestly nothing more than maybe 5 hours a week of reviewing all the links and content in TJNull's Journey to Try Harder. Is that guide awesome? Yes. Was that a productive use of my time? Likely not. That's not to throw shade at TJ. That guide is amazing, especially after he updated it to match the new course layout. And I referenced it a bunch of times throughout my studying to augment areas where I needed to learn more.
Admittedly, I was scared like the countless number of people who hear about the mystical OSCP. I didn't want to fail, so the OCD procrastinator in me thought I needed to learn as much as possible before signing up for the course. When in reality, the best thing for me to do was just sign up for the course. Which leads me to my next point...
It's okay to fail
You might think you're gonna pass the exam on your first attempt. If you do - kudos to you. However, the "word of mouth" pass rate is somewhere around 20-25%. That's the overall pass rate, not even the pass rate on your first attempt - so odds are you're going to fail. That's completely fine. It doesn't matter how many times it takes for you to pass the exam. Offensive Security doesn't list the number of times you took the exam on your certification. There's a reason they now include 2 certification attempts in their LearnOne platform. Failure might be viewed as taboo within American culture, but it's completely normal. Failure isn't something to be ashamed of - failure and quitting might be, but we often mix up the two. If you fail, dust yourself off and get back at it.
Ippsec FTW
Ippsec is infamous within the hacking community. He's got a great Youtube channel with tons of HTB/Vulnhub walkthroughs. I mistakenly avoided his channel when I started the OSCP because I thought I wouldn't want to spoil possible boxes to use as practice. In reality, Offensive Security has enough VMs between the PWK labs and PG to keep you plenty occupied throughout your OSCP journey. I personally focused on the CTF - [*nix|Windows] - [Easy|Medium|Hard] ippsec playlists, but you can't go wrong watching any of his content. Even if you only can listen to the audio, he does a phenomenal job talking through enumeration steps to help reinforce your enumeration tactics.
The "Seinfeld Strategy" is real
I recently came across this article by James Clear which talks about the Seinfeld Strategy. Feel free to read it for the full concept - but the tl;dr is that Jerry Seinfeld became one of the most financially successful comics of all time by writing jokes. The concept - The way to be become a better comic? Create better jokes. How do you create better jokes? Write every day. It's completely transferable to the OSCP. How do you pass the OSCP? By being a better hacker. How do you become a better hacker? Hack every day. The article goes on to talk about how to successfully implement the Seinfeld Strategy, which is "simply" a matter of being consistent. Show up every day. Take the focus off the individual performance - emphasize the process instead. It's more important to show up and put in the work than be proud of how inspired you are or how brilliant your work is every day.
The same goes for pentesting as it does joke writing. Come up with a process that you can complete every day. Yes - every day. I know that's a huge time commitment. Between your regular job, family/friends, and hobbies you probably feel as if there isn't enough time in the week even before you sign up for the OSCP. However, the surest way for success is to allot the time daily. You might have less time on weekdays, but make up for it on weekends. You can't cut corners with the OSCP and expect to pass without putting in the time. Maybe you're one of those 1337 hackers that can, but that's a very small percentage of folks, so odds are you can't. Below is a log of the hours I put in from start to finish over the past 8.5 months. YMMV - your time will likely look different:
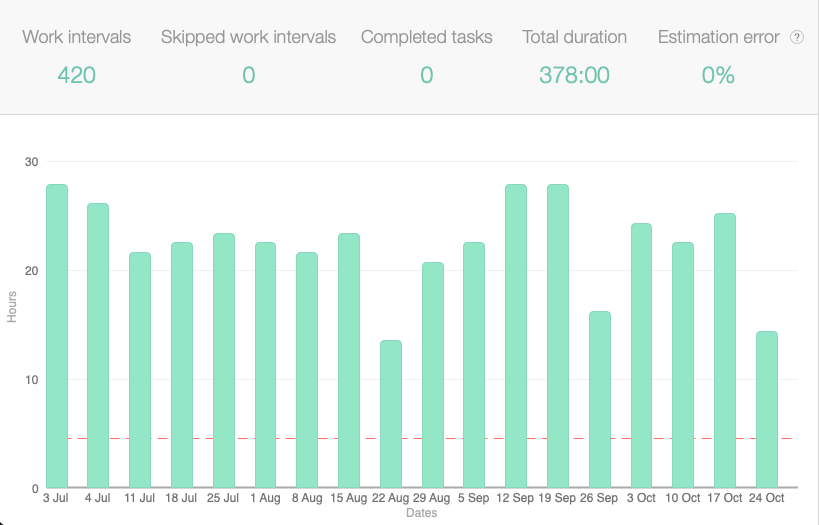
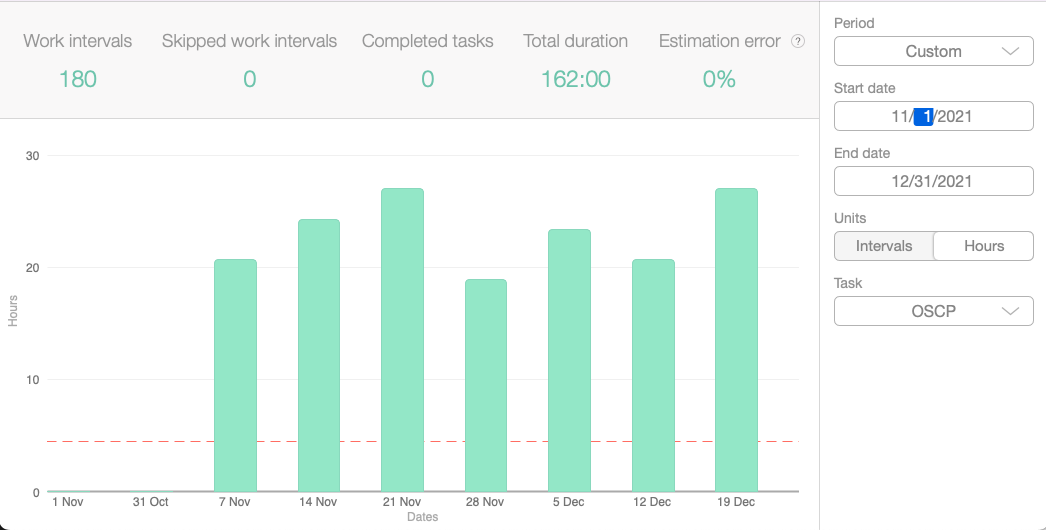
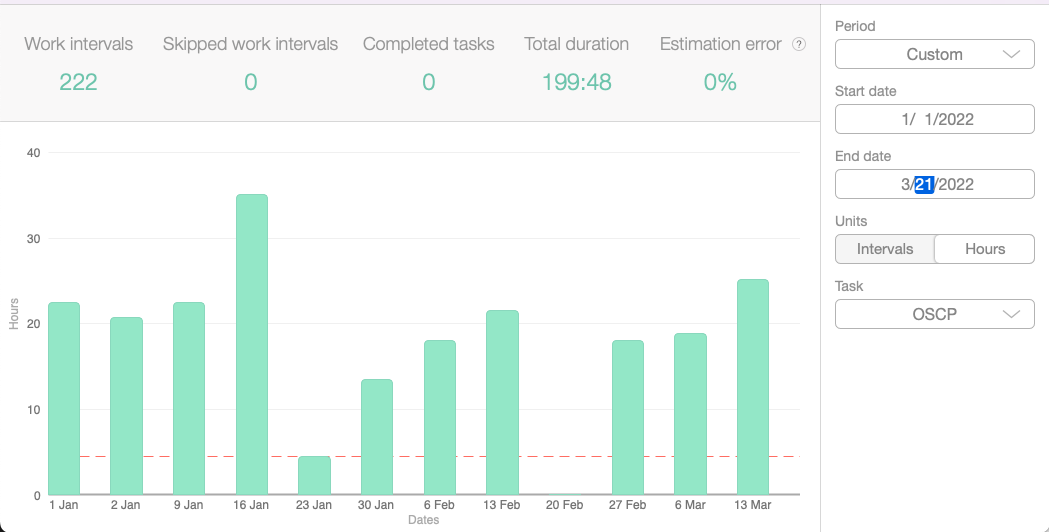
What I can confidently say prepared me for the exam was consistently putting in the time. At first, it was the time spent reviewing the courseware, videos, and completing the exercises. Then - most importantly - it was the time in the labs - (both PWK Lab and PG). The repetition of enumerating 75+ times is what reinforced all of the content. Find a process that works for you to ensure you can show up every day. What worked best for me after reviewing all the courseware/videos/exercises was:
- 1 hour of ippsec videos
- 2-4 hours of PWK Labs/PG Practice
I found it was much easier for me to open a bookmark to the ippsec playlists and hit play than it was to start the day hacking, and then take a break to watch ippsec videos. Ippsec would regularly drop a knowledge bomb or random little nugget that I would then want to try out which helped keep the motivation going.
Note: You likely won't need 750 hours of studying in order to pass. I spent ~150 hours between my second and third exam attempt - which might not have been necessary had I not left 50 points on the table. I also probably spent ~150 hours doing all of the courseware exercises and completing the Lab Report. Most folks pass by putting in ~400 hours of prep work. Granted, YMMV - you may need less than 400 hours, you may need more than 800 hours. It all depends on your prior experience and velocity of learning.
To do the lab report or not do the lab report? That is the question.
Even though I didn't need the report, I think it pays to do the lab report. Is ~150 hours a large amount of time to dedicate to exercises and the lab report creation? Absolutely. Can it be better allocated spent hacking? Perhaps. Did I need the report in order to pass? It doesn't appear so.
The reason I think it's imperative to do though is the flexibility provided going into the exam. I previously talked about the paths to passing with vs. without the lab report previously. Completing the report gave me peace of mind going into the exam knowing I had more options in order to pass, and I wasn't completely dead in the water if I didn't get the AD chain. I'm fairly confident I passed with 80 points (Offensive Security doesn't tell you how many points you scored, only if you passed or failed the exam), which means I could've passed without the lab report. By first appearance it would seem to have be a waste of time to do the lab report. In reality, I think I lucked out with the machines I got where I was able to get the AD chain, 2 footholds and 1 priv esc. My second attempt - had I not overlooked the simplest way to pivot within an AD Environment, and actually checked my UDP scans - would've required the lab report in order to receive a passing grade. However, this is one of my strong convictions loosely held, so I'm not willing to die on the hill that is team lab report.
Previous Lessons Resurfaced and Miscellany
In my first blog post I mentioned a handful of lessons learned. A lot of these still stand true, and I still believe to be true. Below are those points summarized, as well as a few other tips that didn't warrant their own section.
- Learn by doing - time hacking > time reading about hacking. While both are productive, and a step in the right direction - you'll learn more by spending the time hacking VMs than you will reading walkthroughs.
- Don't underestimate your ability to learn- I learned more during my 5 months of prep for the first OSCP exam attempt than I did in all the years in IT prior. The same goes for the 1 month between my first and second exam compared to the 5 months of prep, etc. Each time I was learning more than ever before. Little did I know I had the capacity for more, I just had to put in the time and push myself.
- It takes a village... or a Discord Channel - I probably wouldn't have passed without a few friends/colleagues who were also taking the exam. I was part of a cohort through work that I relied upon to help motivate me throughout the process. However, not everyone will necessarily know a group of folks to lean on during their OSCP journey. That's where the Offensive Security discord channel comes in. Be sure to join it after signing up, and use it as a resource. Use it like the forums to look for previous hints and nudges to boxes you might be stuck on, or even ask for help. And be sure to pay it forward by helping others.
- Random Tools for Success - two productivity tools I wanted to plug that helped me be more efficient: BeFocused (for Mac OS X and iOS) and the "Video Speed Controller" Firefox plugin. The former is a pomodoro timer I used to track all of my progress. I particularly liked how you could schedule custom "work" and "break" times for an interval, and after a certain number of intervals completed you can schedule a longer break. The idea of doing something for 3-5 hours daily might sound daunting, but its far more attainable if you re-frame it as doing something for 54 minutes followed by a 6 minute break 3-5 times. The latter is a Firefox plugin that allows you to speed up videos. This comes in handy for sites that don't allow for faster playback, or if you're one of those weirdos like me who likes to watch videos at 2+x speed.
- Factor Daylight Saving Time to Exam Scheduling - I realized this only effects American exam takers, during a very small window of exam scheduling (typically for exams in the March/November months) - but keep in mind that the times shown when scheduling your exam are adjusted to the current time zone that you're in, but do not factor in DST. It didn't wind up impacting me, since my exam just wound up being 1 hour later than I expected, but I still wanted to share. It'd stink to schedule your exam only to show up and have lost an hour of precious time, or worse have your exam cancelled for a no show.
What's Next
After a much needed break from hacking for a few days, I've still got plenty to learn. I realized about ~4 months into PWK, while the course covers a ton of materials, and provides you with the necessary skills to be a penetration tester, there's still so much to learn. In the short term, I'm hoping to sit for the GIAC GCWN certifiation in the upcoming months. I additionally want to focus on building my cloud skills by taking a few Microsoft Azure (AZ-900, AZ-104) courses. Lastly, I would be remiss to not take another Offensive Security course. Their pedagogy is best in class - on the same level, if not better than SANS. I signed up for WEB-200 with LearnOne back when OS was doing a discounted deal for the LearnOne program. I'm looking forward to experiencing one of Offensive Security's newest courses and eventually obtaining the OSWA.