I took my first attempt at the OSCP, failed, and it was freakin awesome
Lessons learned and ramblings from someone who studied like hell for their first OSCP attempt and failed gloriously.

I failed. I signed up for lab access to formally begin my PWK (Pentesting with Kali) training with Offensive Security on July 3rd. After 166 days, over 503 hours of studying, pwning 47 boxes in the PWK labs, reading/watching the courseware countless times, I took the OSCP exam, and I failed. It was the first time I had failed a professional certification exam and it stung.
Prepping for the Exam
For the less familiar, the OSCP is a 24 hour certification exam to prove competence in ethical hacking or penetration testing. It's well recognized within the infosec community as proof of strong pentesting/hacking skills. Offensive Security, who issues the PWK courseware and OSCP cert has never published overall passing rates for the exam. However, based on word of mouth, it's estimated that the pass rate for the exam is somewhere in the ballpark of 20-25%.
At the beginning the 24 hours, you are given a list of 5-6 computers in which you're tasked to hack. Each computer has a point value associated with it - typically ranging from 10-25 points. In order to pass the exam you need to surpass 70 points. On each computer is usually one or two "flags" or "proofs" that you submit to prove that you've hacked into the system. If you are fortunate enough to surpass the 70 point threshold, you then have another 24 hours to submit a penetration test report. This report documents your steps to gain access to those machines, as well as a summary of each vulnerability, and recommended remediation steps. Typically to prepare for the exam, a student signs up for the course and is given a 800+ page PDF document, over 17 hours of video, and access to a virtual lab environment with 70+ practice machines, which are designed to have specific vulnerabilities to be hacked by the students for various methodologies and processes taught in the courseware. The course isn't intended to teach you "these are the X ways to hack into computers", but rather develop your enumeration methodology for penetration testing - so you develop your own processes for determining the attack surface for a machine and the best way to go about breaking in.
My prerequisite work for even signing up for the PWK Course (PEN-200) started long before July 3rd, 2021. I had the OSCP in my sights for quite some time, but started studying seriously once I saw @TJNull present in BSidesDC 2019 . TJ has an awesome blog post summarizing the talk. From the time of that presentation until July 3rd, 2021 I tried working through as much of the content as possible (it's a lot - kudos to TJ for pulling all that together!). This is a very long winded way of saying, I didn't just sign up for this certification out of the blue, and much more time went into prepping for the exam than the 503 hours I tracked while going through the PWK.
My First Exam Experience
Leading up to my exam - in the "old" aka non-AD exam format - I was feeling great. I had read the courseware cover to cover (and referenced it countless times), watched all of the provided videos, and pwned - or hacked into - 47 different machines in the lab. I had even had ~30 coworkers who were also studying for the exam as a mini-community to lean and learn from, in addition to the Offensive Security Forums. I had completed the Lab Report for the additional 5 bonus points - including documenting each and every required exercise in the PWK courseware - more so out of OCD and FOMO than anything.
I knew the task at hand - I'd have 5 boxes to hack - one 25 pointer which was for sure going to developing a buffer overflow exploit, another 25 point box whose attack vector was not a buffer overflow, two 20-point boxes, and a 10-point box. I was feeling fortunate, but also a tad bit of pressure, as I was going to be one of the last students taking the exam in this format, as Offensive Security had recently announced that the exam format was going to change on January 11th, 2022. I had previously prepared for my exam without a major focus on Active Directory (though I did pwn both chains in the lab).
Once my exam started, everything was going swimmingly. I kicked off my initial enumeration scans on the non-buffer overflow system, and began attacking the buffer overflow box. In less than two hours, I had gotten root level access and had reached 30 points (25 for the box and 5 points for the Lab Report). That was the pinnacle of my 24 hour period, and what I'd imagine was a microcosm of what "peaking in high school" must've felt like.
For the remaining ~22 hours I struggled to even gain a foothold on any of the other 4 machines. I took a ~5 hour break to sleep as I knew going into it I wasn't the type of hacker that functioned well sleep deprived. Compared to my time in the lab, it felt as if I was a complete train wreck. Services and files I had enumerated were some of the ones I had attacked the least while in the lab. Couple that with my limited experience in hacking multiple machines concurrently, along with an aggressive and condensed timeline, and I had crumbled. I had even set timers for myself to take regular breaks, as well as allotted 30 minute increments to hack different services within a box, and rotate on each box every 2 hours.
I had come to the realization I wasn't going to pass a few hours prior to the exam ending, as I hadn't gotten a foothold anywhere, and my likelihood of passing was falling precipitously with each moment of not getting a foothold anywhere. That's when the feeling of failure and doubt crept in. All of that time spent prepping - all of the long hours after work, all of the weekends dedicated to PWK - felt as if they were wasted. I toiled in my failure for a few hours, until I realized doing so wasn't going to improve anything. It wasn't going to get me OSCP certified, and it wasn't going to prepare me better for my next attempt. The longer I toiled, the longer I delayed from achieving my goal.
What I Learned from Failure
I write this not to fish for sympathy, but so that others can learn from my mistakes. I read tons of blog/forum posts and reddit threads about how to best prepare for the actual exam. There's something to learn from each and every one of those perspectives. The purpose of this post is to share and add to those perspectives so people can learn from my experiences. Some of these tips you'll see as recommendations from others, and maybe one or two are new insights. But my hope is to help contribute to the community that has given me so much over the years.
Take "Practice Tests"
Tip: Set aside 24 hours and try to simulate the exam. Pick 6 different boxes (assuming you're taking the new exam format), follow the same point allocation as the exam, and try to surpass the 70 point minimum threshold over the 24-hour period.
The How: I had heard this recommendation about a week or two prior to my exam. I unfortunately wasn't able to get a full practice test in before my exam, but definitely think it would've helped.
If you can actually dedicate an uninterrupted 24 hours to this, more power to you. But I think it could be equally as productive if you allot 24 1-hour blocks over a few days (the fewer the better). Of those 6 machines, 3 should be of "20-point" value and remaining 3 should be an AD (Active Directory) style attack. I haven't looked into the best way to practice testing against the AD set, but I'm open to suggestions!
In terms of where to get your victim machines, for the non-AD boxes, Offensive Security's own Proving Grounds is a good place to start. TJNull's Trophy Room has a great list of recommended boxes from both PG Play and PG Practice for OSCP. PG is great, as it has it's own point values for each of the machines listed, so you might be able to use that as a barometer for which machines to pick. That being said, YMMV since the exam has yet to be released at the time of this writing.
If you signed up for the PWK course through the LearnOne program you'll automatically have access to Proving Grounds Practice. If for whatever reason you don't have access to Proving Grounds, you can always check out HackTheBox or VulnHub and use TJNull's guide as barometer for candidate machines.
Keep in mind that you might be able to do this, that this isn't a perfect supplement for the actual exam. You'll likely have less than 24-hours to take the exam if you're allotting time for breaks, sleep, etc. Additionally, if you're taking the exam over multiple days, you might be - consciously or not - thinking about next steps even though your 24 hour timer isn't running. Some sites that you might use for the Practice Exam (i.e. PG) also limit you to only having one machine online at a time as well, which is a nuanced difference from the actual exam.
Disclaimer: Nothing is as good of a substitute for learning the PWK material than the machines within the PWK labs. If you haven't haven't put in the time in the labs, then practice tests likely will not help you. If you're wondering how much lab time you should put in before taking the exam, I'd recommend reading OS' own Path to Success in the PWK Labs.
The Why: The reason behind doing is is to familiarize yourself with the exam format. You'll need to be comfortable enumerating multiple machines concurrently. Both from a literal sense - in kicking off scans and enumerating on services-and also a mental sense- being able to remember that Box A's HTTP service might be vulnerable, and Box B's SMB service might be vulnerable. You'll need to be able to be comfortable handling all of these activities without getting overwhelmed or confused.
Organization is Key
Tip: When you are enumerating, be sure to document everything you do.
The How: Make sure you're documenting both each command you run, as well as the command output. I was only documenting the output, and I noticed in retrospect I ran the same commands multiple times over different time periods.
Try to keep those notes organized, both in the terminal, or in any note taking tool that you're using (i.e. Joplin, Cherry Tree, OneNote). There's tons of OSCP/pentesting templates in many different tools - I personally use TJNull's Joplin Template. Use this template during your time in the lab to familiarize yourself with it, as well as to customize it to your enumeration methods.
For your terminal for the exam, I'd recommend a terminal tab per box, and tmux session (or terminal multiplexer of your choosing) running in each, with a tmux tab per service. This helps for organization, especially if you're using tmux/terminal logging for easy reference.
Also, keep a section in your notes that lists 1) each service; 2) things/ways to enumerate that service; 3) activities completed the service already. This will be helpful, especially if you have the same services on different boxes during the exam.
The exam challenges you not only on your technical skills but also your time management skills. Develop a system to rotate through services on each machine as well as rotating through each machine during your initial recon. While you may have initial hunches about which is the likely attack vector, you may want to hedge against falling down one of the many OSCP's infamous rabbit holes.
The Why: This tip is simple and obvious, but was hard for me to do when the rubber hit the road. During the exam, when things started going sideways and I was feeling like I was chasing down rabbit holes, I stopped documenting the right way. This was a snowball effect, as my disorganization took me out of focus. In retrospect, it led to me rerunning the same enumeration techniques more times than necessary and wasted much of my precious time.
Automate What You Can
Tip: Script/Automate things that you do or expect to do which are repetitive.
The How: So this is actually beneficial to do towards the end of your time in the PWK labs. Personally, I extracted a lot of value out of manually enumerating for the entirety of my time in the PWK labs. It helped reinforce how to properly run the various command as well as what each of the various flags mean.
However, after some time in the labs and you may fall into habits of running a set of the same commands for each different service that you come across. Try to script it so you can do that initial enumeration of the service as streamlined as possible. Whether it's something as simple as an alias for searchsploit to save you keystrokes, or a bash/python script to pull the port numbers running an HTTP service from your initial nmap scan and kick off dirsearch. It can start off simple, and iteratively improve over time. Your goal shouldn't be to develop the perfect script which will document everything you need, but progress towards less time repeating the same steps. Then more time can be allocated towards analysis, while decreasing the likelihood of mistakes.
The Why: You won't be able to script every possible enumeration step. You likely will need to follow up those results. But it will save you time for that initial recon. You'll be then able to use those results and that additional time to tailor further enumeration steps. You'll want to spend your time wisely, which is better spent analyzing your results than fixing that same enum4linux-ng command you always run when you see an SMB service is present but fat fingered by mistake.
Do you really need to type out, or even copy and paste the same nmap commands for your initial recon on each box? Maybe the first few boxes you attack in the lab, but not come exam time. You also will become a better hacker by having the opportunity to develop your coding skills.
Learn to Learn
Tip: Always strive to be looking for ways to enumerate better/faster. You're not expected to be an expert on how to hack every possible service. However you are expected to be an expert on how to research and learn things expediently. Don't just rely upon your pwned box count in the labs as a metric for your metric of how well you're learning.
The How/The Why: That being said, your best bet for success is spending time in the PWK labs. I know, its a bit of a paradox, but it's a bit more nuanced.
HTB Academy has an interesting course on learning where they cover the concept of the Learning Pyramid. Essentially, the theory is that it's best to learn by doing. This aligns with the countless blog posts (this one included) which encourages students to spend as much time as possible in the PWK labs. That being said, the Learning Pyramid also states that if you can't learn by doing, there's also value from learning by reading/watching/listeneing. If you don't have access to the labs for whatever reason, you can still learn. Spend time in HTB/Vulnhub/TryHackMe or any of the other CTF sites. While some boxes might not be at the difficultly level of those in the PWK, it helps to get exposure to as many services and configurations as possible.
Try not to use forum posts or walkthroughs as help when you are practicing. However, there still is value in reading/watching walkthroughs (Ippsec has an awesome Youtube Channel) even of machines you might not try to hack. While it might not be the PWK prescribed method, it still helps to get exposure to different methods and ways of doing things. Watch or listen to those walkthroughs if you've got down time. Supplement the walkthroughs for podcasts or music you might listen to during the day. Ippsec does an amazing job not only of showing you what he is doing, but talking through his thought process and why he is doing things.
Gamify the Exam
Tip: Before you sit for the exam, be sure to "gamify" the exam analyze how you're going to get to 70+ points.
The How: I don't necessarily have answers for the questions below. However, I don't think anyone will. What works best is extremely personalized, and to you. But it's important to think through:
- Will I do the practice Lab Report?
The new point structure is as follows (as of Dec 2021):
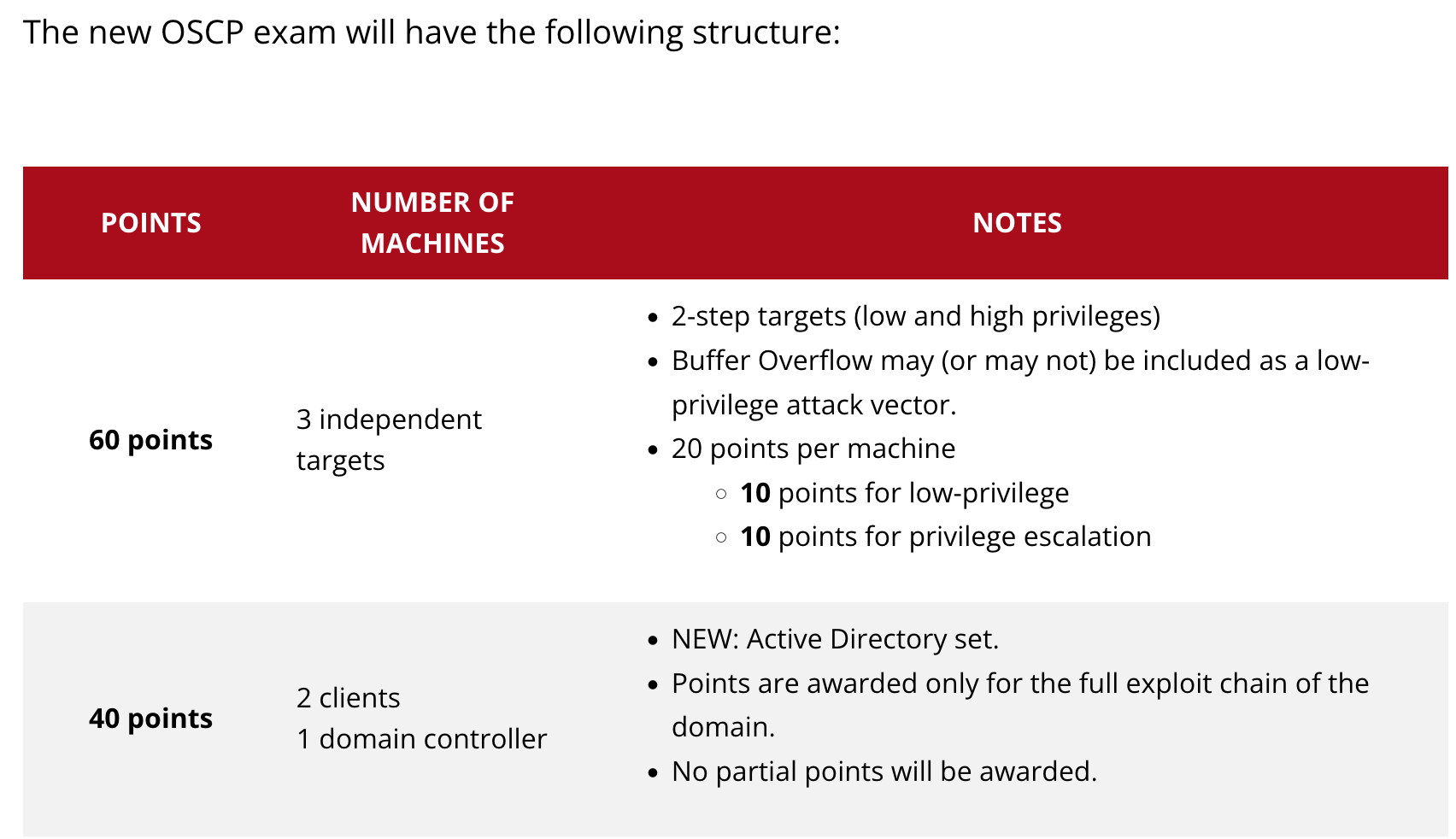
The new exam format gives you 10 total points to complete the lab report.
The main avenues you have for passing (at a minimum) with the lab report are:
- Lab Report Option #1: 3 total boxes - 3 independent targets w/ full access (low-privilege AND privilege escalation -20 points each) + Lab Report
- Lab Report Option #2: 4 total boxes - Full AD Chain (40 points) + 1 independent target w/ full access (2o points) + Lab Report
- Lab Report Option #3: 5 total boxes - Full AD chain (40 points) + 2 independent targets w/ low priv access (10 points each) + Lab Report
Without the lab report, your options to pass include, at a minimum:
- No Lab Report Option #1: 5 total boxes - Full AD Chain (40 points) + 1 independent target w/ full access (20 points) + 1 independent target w/ low priv (10 points)
- No Lab Report Option #2: 6 total boxes - Full AD Chain (40 points) + 3 independent targets w/low priv access (1o points each)
The lab report could be the difference between needing to hack 3 boxes, versus hacking the entire lab.
Keep in mind, it will take you a decent amount of time to complete the Lab Report. I didn't keep explicit metrics around how long it took me. However my estimate is that it took approximately 120 hours to complete. Estimate based on 50% of my time going through the courseware, plus the ~20 hours it took to write up the actual report. That could be a lot of lab time for some folks. So it's up to you to decide if the juice is worth the squeeze.
Based on how you answer question #1, you should determine:
2. Where do you start attacking first? How do I complete my initial enumeration?
This question was a bit easier to understand in the old exam format (i.e. do you do the buffer overflow? If so, do you save it till the very end or knock it out first?). I look forward to hearing from others their thoughts once folks start taking the new exam format and documenting their thoughts. But it helps to at least develop an initial gameplan for when you start. You'll need to be flexible and willing to pivot from that plan, but it helps to do this thought exercise rather than going in blind.
Iterative Enumeration
Tip: Be sure to develop a methodology that allows you to enumerate in waves.
The How: Develop a methodology for doing an initial pass of sesrvices. You may have certain resources (i.e. dirsearch) that malfunction when running concurrently. Script it if you can (going back to an earlier tip).
The Why: It helps to have an initial enumeration on your services to drive your next steps. However, you don't want to completely compromise diligence for speed. Figure out what work best for you to balance the two.
During my exam I had made the mistake of using a hefty wordlist (along with extension appending) that took 1+ hour to complete. I also had performance issues by running too many instances/threads of dirsearch concurrently. I forgot how often I would kick off certai enumeration steps and walk away for some time. It was great for the lab, but not great when you're in a time crunch.
Whats Next?
After I spent a few hours licking my wounds, taking a weekend off from my failed attempt, I've decided to sign up for my next exam attempt. I've been fortunate enough to talk to colleagues, friends, and members on the OS Discord channel who also failed and have given me a positive outlook on the future. While there's no other way to bluntly describe the feeling of failing the OSCP exam other than "it sucks", it's also fairly common.
That being said, the amount I have grown and learned over the past 5+ months has been astounding. While the PWK has required a crazy amount of my time, it has been time well spent. Looking back over that time, it has been both humbling and exciting.
So, while I might not have achieved my goal, I'm looking forward to continuing to grow and getting to that day where I do pass. Whether its after another month of preparation, or 3+ months and hacking every box I can get my hands on from Proving Grounds, HTB, and VulnHub - I know I'll get there. My PWK/OSCP journey has jumpstarted my journey of lifelong learning within infosec. Which is why failing the OSCP was pretty freakin awesome.