enumnotes: CLI + md Pentest Notes = pretty colors
Overview of the my terminal based penetration testing note tool
Below is a post explaining the backstory to my first GitHub project enumnotes. You can go directly to my Github Repo and read the README.md to get the tl;dr version. It's nothing fancy or super complicated, but I wanted to give more context to the tool for more novice users, or provide material for insomniacs to overcome their affliction.
Why Create it?
It basically comes down to a few factors:
- Give back to the community
- Realizing the Challenges of Joplin
- Obsidian = Mardown files FTW
- A desire for daily GitHub commits
I'll start it off by saying, this tool isn't revolutionary. In fact, you'll find many resources like this one. It's simply another way to format Pentest enumeration templates/notes. Additionally, enumnotes itself even builds off another resource, @TJ_Null's awesome Joplin Pentest Template. I first came across TJ's template when I was reviewing his Journey to Try Harder blog post about prepping for the OSCP. I personally used TJ's Joplin template (v 1.0) to help me get through the PWK material and pass the OSCP! It's an awesome resource! This also obviously implies used Joplin to pass the OSCP! It's a very suitable solution enumnotes is the content in a different format, and my attempt to give back to the community.
Challenges of Joplin
There are pros and cons of every application, and Joplin is no different. This isn't a post intended to dunk on Joplin, more just explain some of the challenges I faced while using it. After using Joplin for a while I noticed some of the downsides.
- Mainly, the data is stored in a sqlite database, so Joplin needs to be open in order to edit any files easily.
- Secondly, at times it was advantageous to group enumeration of boxes by the enumeration step, but it also sometimes was unnecessarily complex.
- I also ran into issue when I would try and replicate the Joplin notebook for other uses (i.e. PWK, Proving Grounds, HTB, etc.). It required a lot of unnecessary data redundancy, increasing the file size, or time to go through the updated file to remove the additional data
The Pivot to Obsidian
After getting used to Joplin, I saw Ippsec's two videos: one on the advantages of Obsidian and another showcasing Obsidian's Timeline feature. In the first video he shows a useful process for organizing notes while enumerating targets. The second video more so showcases a cool feature within Obisidian to have a visual representation showing the attack chain used to enumerate and exploit a box.
After deciding to make a switch to Obsidian though, I didn't want to lose the awesome notes TJ had provided. Furthermore, since the initial download, I had tweaked and personalized the notes for my use. It also seemed redundant to have both Obisidan and Joplin open simultaneously.
GitHub commits
Lastly, I wanted to get in the habit of actually using my GitHub account. For too long I procrastinated on creating something, or contributing towards an existing project. As I've talked about in a previous blog post, the Seinfeld Strategy is real. I was tired of referencing my GitHub on my resume and other places and having nothing to show for it. At least I now have something. While its a simple bash script, its better than nothing.
Why enumnotes?
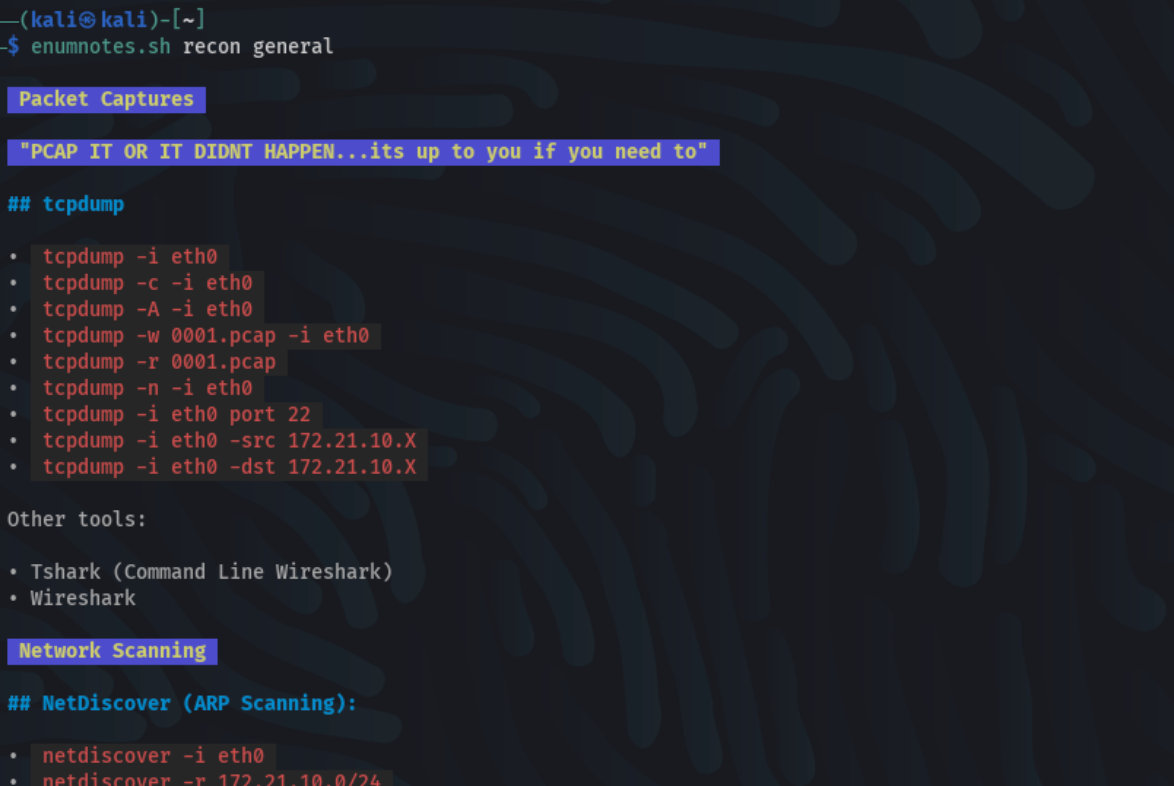
- Markdown FTW - first and foremost, all of the data resides within markdown files. I've gone through and tried to format the data logically - with proper headers/sub-headers for sections, and denoting code with the proper formatting.
.md+glow= BAM - I foundglow, a command line tool that render's markdown on the command line in pretty colors, and extremely customizable. Additionally the script allows for the use of theglowflags, so functionality ofglowsuch as paginate still works!
- So Fresh & So Clean - not only visually aesthetic, but this avoids the need for another program open just to view your notes, or hog up precious real estate persistently. Odds are you'll always have a command line open. Efficient!
- Customizable - The entire application is customizable to your liking! Think some notes are garbage? Edit the files, get rid of it. Think some sections are missing? Add new files and tweak the main script. Think its silly to read your notes on the command line? Open the files in Obsidian or your favorite text editor.
- Collaborative - easy to share notes with friends or coworkers! Shared drive, GitHub, you name it. Markdown files make it easy to track changes and edits.
- Easy Backups/Edits - It's easy to backup and edit any of these files, as they are simple text files. Regular backups of your pentesting are integral part of your OSCP journey in case anything is lost by mistake. See m0nk3h's OSCP Lab Tips & Tricks for more detail and other helpful pointers for the journey!
- Helpful Error Messages - don't know how to run the tool? just run
enumnotes.shand an informative message will remind you of the syntax and groupings of enumeration notes. This also works when entering categories, as well as invalid categories and subcategories.
Installing
Installing enumnotes is rather simple. Clone the git repository, and launch the setup.sh script within the cloned repo. The setup script checks if glow is installed, and if not downloads it to your ~/Downloads directory, and installs it. Enumnotes is then recursively copied to the /usr/local/bin/ directory, and a symlink is created so you can run enumnotes.sh without needing to update your PATH, or specify the absolute path.
Be sure to check out the Setup Notes on the Github repo to ensure you're following the proper setup instructions.
Make it Your Own
Below are a few ideas on how you might want to customize enumnotes to your own liking:
- Edit existing files to add your own notes
- Add additional files to the directories
- edit
enumnotes.shto add a category, subcategory, or file to be read on a command - Edit
glowconfiguration to change the colors displayed when runningenumnotes
Future Enhancements
Below are a few ideas I have for future enhancements. No timeline or guarantee of implementing them, but I realize this is far from a fully baked product.
- Add additional pentesting domains (i.e. cloud, web, etc.)
- Search functionality - be able to look for any files that contain a specific search phrase
- System/Target IP replacements - have any references of the host/target IP address, domain name, etc. be updated based on user supplied data.
Enjoy
Hopefully you find as much value in the tool as I do! At the very least, this is an easy way for me to share my enumeration notes with all my various devices.