Natas4--> Natas6
Continuing the walkthroughs for the overthewire web challenges.

Review & Introduction
We're continuing our series of the Natas challenges. The previous post covers the challenges to get us to this point, as well as an overview of the walkthrough format.
Proxy Setup
You'll need to setup a proxy for use for the next few challenges. In penetration testing, there are strong opinions of which tool, extension, or the like is premier. This post isn't intended to contribute to that conversation or answer that debate. It's important to realize, that as a penetration tester it's best to get comfortable using different tools. Just because the walkthroughs may show using Burpsuite, doesn't mean the solution can't be solved using Zap. Just because I may be using SwitchyOmega, doesn't mean either FoxyProxy or even direct Firefox configs are inferior.
The internet has plenty of walkthroughs for installing and configuring a proxy. I'll assume you have done some work with the google machines to have that configured.
Natas4 --> Natas5
Website: http://natas4.natas.labs.overthewire.org/; Access Credentials: natas4:tKOcJIbzM4lTs8hbCmzn5Zr4434fGZQm
After browsing to the page, read the main content on the page, which specifies "authorized users should come only from 'http://natas5.natas.labs.overthewire.org/'". Fire up BurpSuite, or the proxy of your choice, if you haven't already. If you've had the proxy running before visiting the site, and assuming proxy interception has been turned off, navigate to the Proxy tab and select the HTTP history sub-tab. Locate the GET request which went to the root directory of the website. Right click within the body of the request and select Send to Repeater.
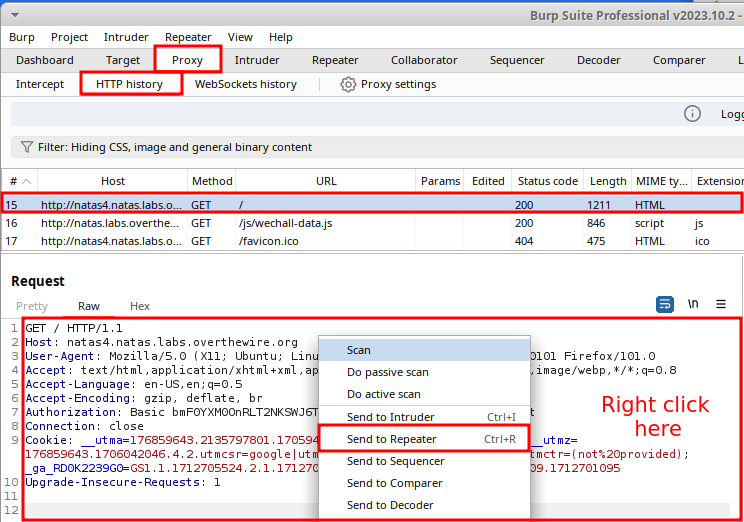
Once the request is sent, the Repeater tab should change to orange highlighted text. Select the tab, and it should open directly to the request you sent. You can click the Send button (or hit CTRL+Space) to send the request and see the server response. It's not mandatory, but a good habit I was recommended and have adopted.
Edit the request and add a Referer header. The Referer header (yes that's the proper spelling, blame the RFC) is intended for a server to identify the referring page that is making the request. This can be either the absolute, or partial/relative URI from where the request has been made. You can read the RFC, the MDN documentation, or the Portswigger Academy explanation for a more comprehensive explanation. Add a new line to the HTTP Headers, and write in Referer: http://natas5.natas.labs.overthewire.org/. Send the request, and the password returns.
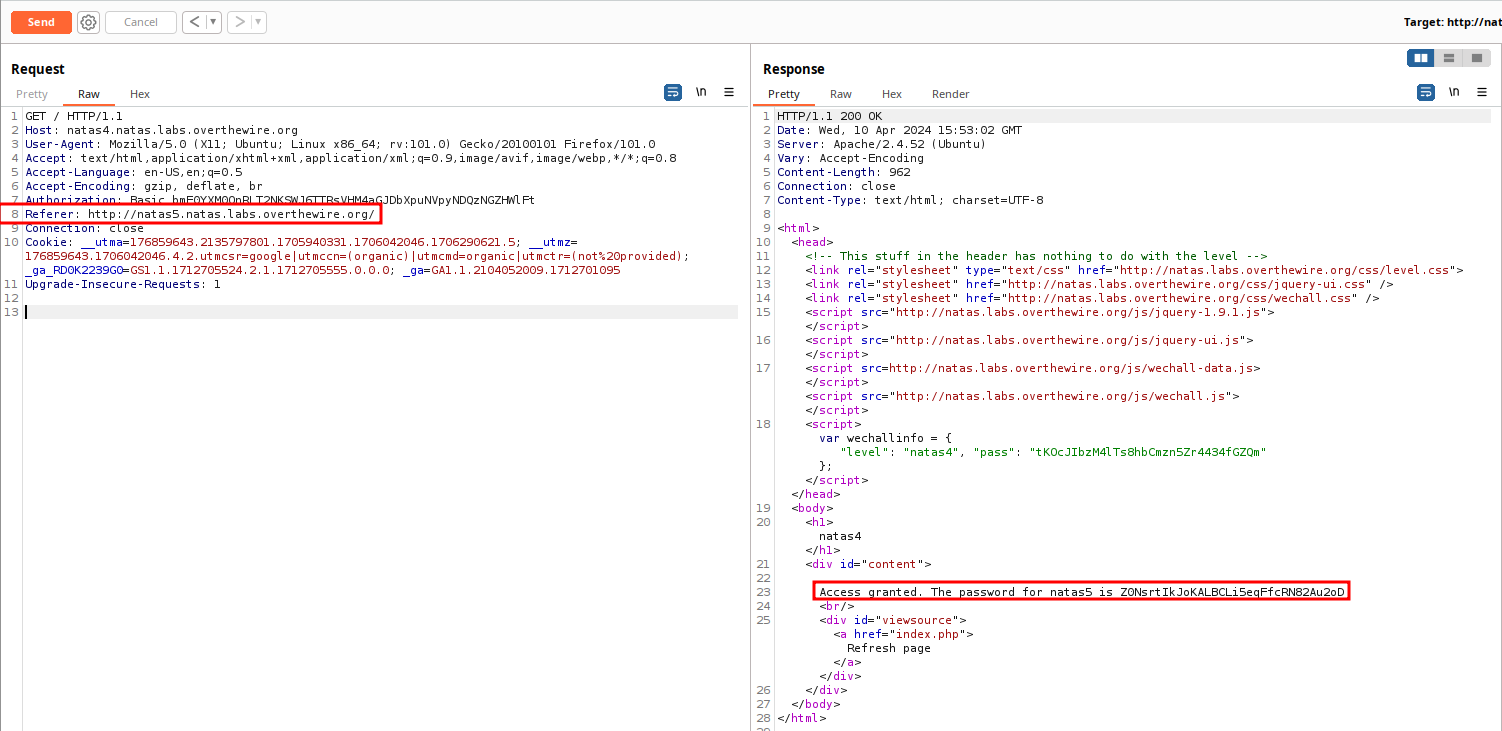
Natas5-->Natas6
Website: http://natas5.natas.labs.overthewire.org/ ; Access Credentials: natas5:Z0NsrtIkJoKALBCLi5eqFfcRN82Au2oD
After authentication, the webpage mentions "You are not logged in". Go into you proxy and look at the HTTP history. Within Burp, this can be found by navigating to the Proxy tab, and from there the HTTP history sub-tab. Locate the GET request to the root URI. Note that the server response includes a cookie value of: Set-Cookie: loggedin=0. If you refresh the browser, and look at the updated GET request, it will include that cookie value in the request's Cookie header.
Since we used Repeater for the last challenge, we'll diversify our proxy functionality and edit the request in flight. Turn on hte proxy by navigating to the Proxy tab, and select the Intercept sub-tab. Assuming that interception is off, click on Incercept is off, which will turn on the Interception proxy, and change the color of the button. Refresh the page, and a new GET request will appear in the interception proxy.
- Edit the value of the
loggedincookie to equal 1 - Forward along the proxy by clicking Forward, or clicking on Incerception is on to turn off the interception proxy and send along the request - and all subsequent requests.
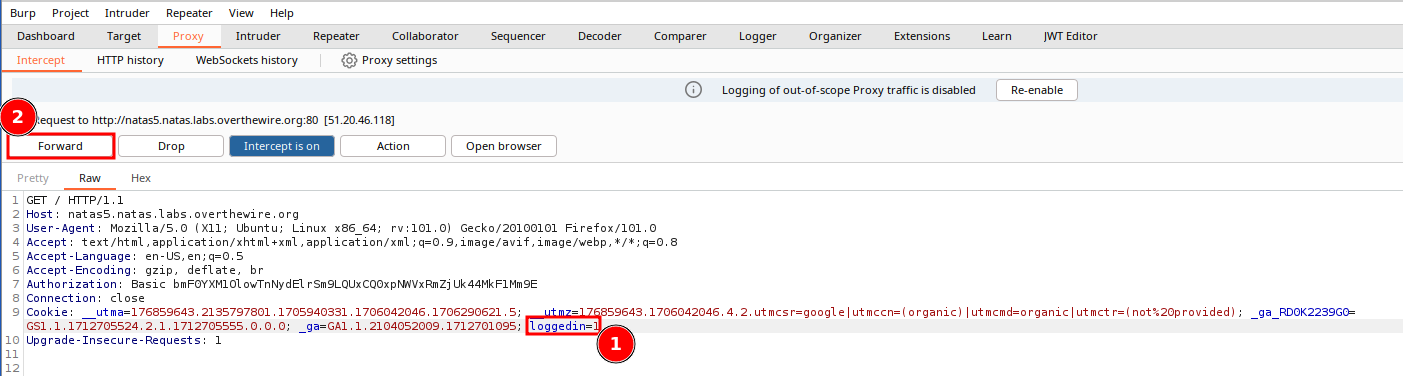
The browser will return the updated page, along with the password, fOIvE0MDtPTgRhqmmvvAOt2EfXR6uQgR.
Summary
Another two challenges complete! We dabbled a bit more with curl, and got some exposure to manipulating HTTP request headers via Burp.
Alternative Methods
curl Alternative
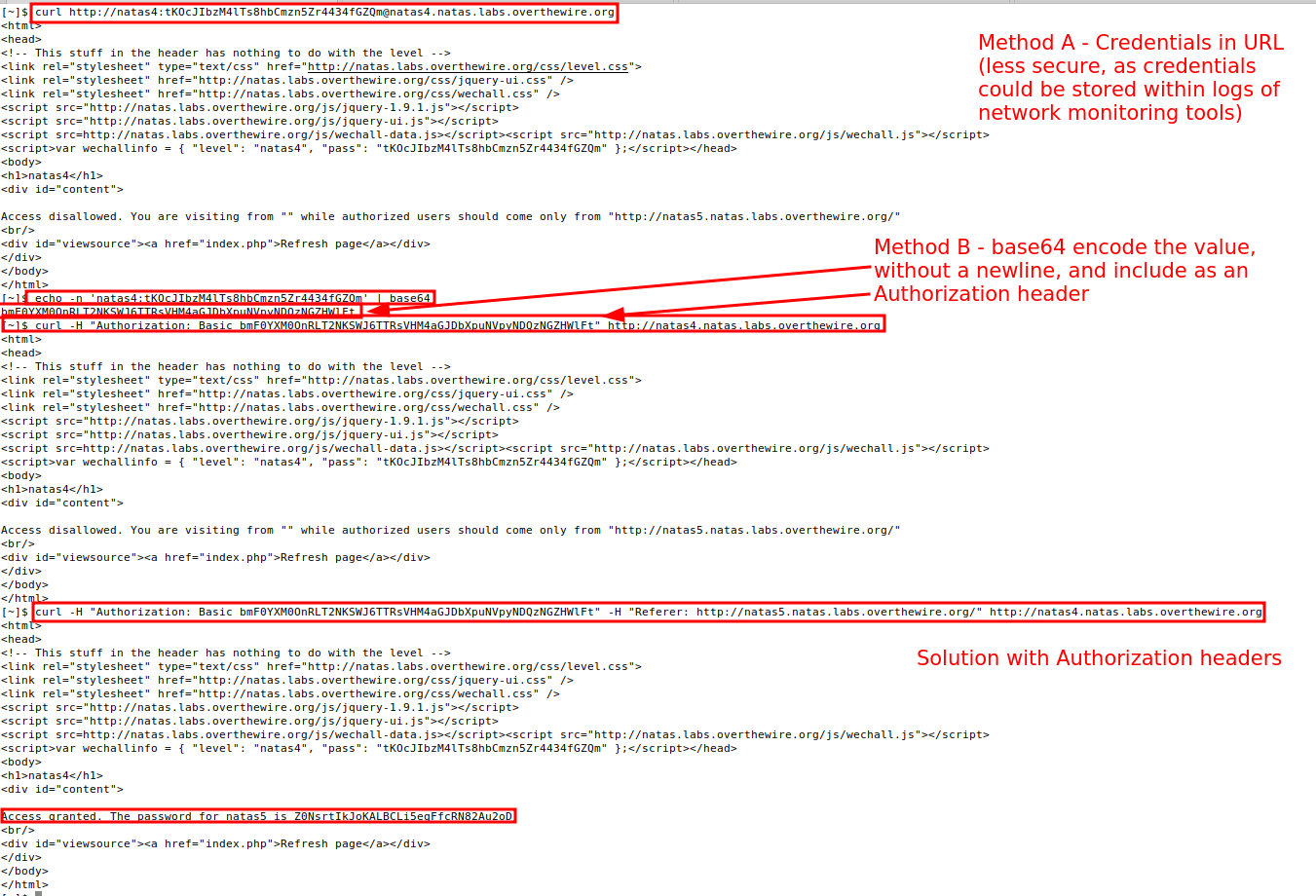
You can solve the Natas4 – > Natas5 challenge using the command line. In a previous challenge, we used curl with the -u user:pass flag. Whats occurring under the hood is curl is taking that user:pass combination, base64 encoding it, and adding an Authorization header in the format of: Authorization: Basic userpassb64encodedvalue for each request. Check the RFC (RFC#7617) for the full details if you so desire. A less secure, but still functional method, is to provide the credentials prepended within the website's URL. Alternatively, you can base64 the credentials without a newline (-n), and append the value to a Authorization: Basic header.
Other Ideas
- For Natas4-->Natas5 - Intercept and edit the request in real time, rather than using Burp Repeater.
- For Natas5-->Natas6 - send the
loggedin=1cookie via curl - Use an alternative proxy, i.e. Zap.